 文章
文章
 身份和安全性
身份和安全性
| |||
|
在涉及 Oracle WebLogic 和 Oracle Service Bus 的架构中使用 Oracle Security Token Service
作者:Ronaldo Fernandes
使用 Oracle Security Token Service 生成安全断言标记语言 (SAML) 令牌。
2014 年 1 月
下载
Oracle Security Token Service
Oracle WebLogic Server
Oracle Service Bus
最近,我对 Oracle Security Token Service (OSTS) 在涉及 Oracle 融合中间件(主要是 Oracle WebLogic Server (WLS)、Oracle Web Service Manager (OWSM) 和 Oracle Service Bus (OSB))的架构中的使用进行了概念验证。许多安全场景都可以使用 OSTS,但最初目标是使用 OSTS 生成安全断言标记语言 (SAML) 令牌,以在 WLS 和 OSB 之间提供一次性登录。本文介绍该解决方案的实施步骤。
情景
该解决方案是在 OWSM 上实现的,用到了 OSB 11g (11.1.1.6)、Oracle Access Manager (OAM) 11gR2 (11.1.2) 和 WLS 11g (10.3.6)。Security Token Service (STS) 创建并验证安全令牌,它使用 WS-Trust 等协议,在安全基础架构中充当集中点,并简化异质环境间的身份传播。
OSTS 是一个 Oracle 身份管理访问管理解决方案。有关 OSTS 的详细信息,请查阅 Oracle 融合中间件 A 团队解决方案架构师 Andre Correa 的以下文章:
概念验证要求 WLS 上的客户端使用 SAML 访问 OSB 提供的服务。SAML 断言应由 OSTS 生成。
WLS 可以使用 WS-Trust 策略并与 OSTS 通信,但 OSB 11g 仍然不支持 WS-Trust 策略。要解决此问题,请将 OSB 配置为信任 OSTS 证书签名的消息。以下是完整场景:

图 1:OSTS 场景
- 用户使用 BASIC 身份验证调用 WLS 上的 Web 服务
- WLS 对用户身份进行验证并使用请求安全令牌 (RST) 调用 OSTS
- OSTS 验证 RST
- OSTS 返回包含 SAML 令牌的请求安全令牌响应 (RSTR)
- WLS 从 RSTR 获取 SAML 断言调用 OSB 上的 Web 服务
- OSB 对照 OSTS 证书验证 SAML 断言
- OSB 向 WLS 返回响应
- WLS 向 OSB 返回响应
配置
Oracle Security Token Service
访问 OAM 控制台(例如 http://<host>:<port>/oamconsole>),确保已启用 STS:

图 2:OSTS 已启用
请求方
请求方代表需要调用服务的客户端。可以为请求配置“签名和加密”,但在本场景中并无此必要。
在 Security Token Service 部分中,访问 Partners > Requesters,使用以下配置创建一个请求方:
- Partner Name:Test Client
- Partner Profile:request-profiler

图 3:创建请求方
依赖方
依赖方代表要访问的资源。在此场景中,这代表 OSB 提供的服务端点。
使用以下配置创建一个依赖方:
- Partner Name:OSB_Test
- Partner Profile:Relying Party
- Resource Pattern:
https://osb.oracleads.com:8012/Testsec/Proxy_Service/Test - Description:OSB Test Service
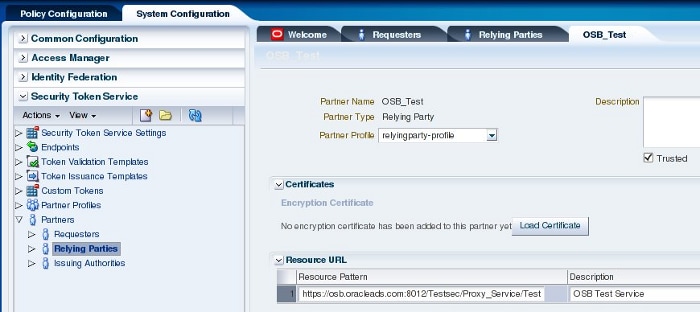
图 4:创建依赖方
颁发机构
颁发机构是负责颁发所需令牌的实体。
使用以下配置创建一个颁发机构:
- Partner Name:Test Issue Authority
- Issuer ID:TestIssuerID
- Partner Profile:issuingauthority-profile
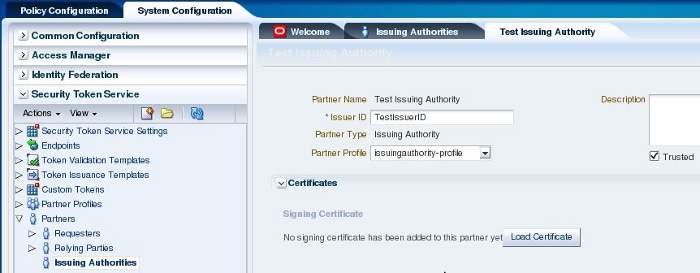
图 5:创建颁发机构
合作伙伴配置文件 (issuingauthority-profile) 颁发 SAML 令牌。
令牌颁发模板
令牌颁发模板定义如何构造令牌。在本例中,我们使用模板 saml20-issuance-template。
此模板定义断言颁发方。该值稍后将用于 OSB 代理服务安全。该模板还告知将如何验证代理用户。因为将对照 WebLogic 领域检查此用户,在本例中,将 Name Identifier Format 值更改为 Unspecified,将 Name Identifier User Attribute 值更改为 givenname。

图 6:SAML 2.0 颁发模板
应用程序域
应用程序域定义资源的访问规则。
使用名称 Services 创建一个应用程序域:
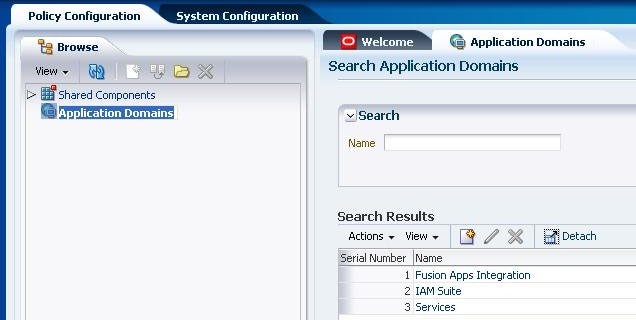
图 7:创建应用程序域
这是访问应用程序域 Services、映射要访问的资源 (OSB Web Service) 和访问规则所必需的。
资源
访问 Services 应用程序域。在 Resources 选项卡中,创建一个资源,它引用先前创建的资源:
- Type:TokenServiceRP
- Resource URL:OSB_Test
- Operations:All、ISSUE

图 8:创建资源
令牌颁发策略
在 Token Issuance Policies 选项卡中,创建一个没有授权限制的策略:
- Name(图 9):Test Token Issuance Policy
- Resources(图 10):OSB_Test
- Conditions(图 11):
- Name:TRUE
- Type:true
- Allow Rule(图 12):TRUE (True)

图 9:创建令牌颁发策略

图 10:创建令牌颁发策略资源
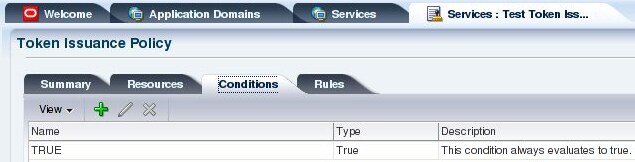
图 11:创建令牌颁发策略条件

图 12:创建令牌颁发策略规则
WebLogic 控制台
访问 OSTS WebLogic 控制台,创建一个名为 pocsamlclient 的用户。
按照前面的定义,OSTS 将根据属性 givenname 验证用户名。因此将此属性的值更改为 pocsamlclient:

图 13:创建用户
Oracle Service Bus
创建一个名为 Test 的代理服务,路径为 Testsec/Proxy_Service:
Testsec/Proxy_Service/Test
代理服务接收并返回一个简单文本:
<xsd:schema targetNamespace="http://www.example.org/Test/">
<xsd:element name="hello">
<xsd:complexType>
<xsd:sequence>
<xsd:element name="in" type="xsd:string"/>
</xsd:sequence>
</xsd:complexType>
</xsd:element>
<xsd:element name="helloResponse">
<xsd:complexType>
<xsd:sequence>
<xsd:element name="out" type="xsd:string"/>
</xsd:sequence>
</xsd:complexType>
</xsd:element>
</xsd:schema>
代理将接收一条包含安全头的消息。删除这些头,然后用替换节点将回答发送回客户端:
- XPath: .
- In Variable:header
- Expression:
<soap-env:Header/>
用一条消息替换响应,用户名串接在原始文本上。
示例:
<soap-env:Body>
<ns0:helloResponse>
<out>{ concat('username = ', $inbound/ctx:security/ctx:messageLevelClient,
', text = ', $hello1/in) }</out>
</ns0:helloResponse>
</soap-env:Body>
将此策略与代理服务关联:
oracle/wss-saml20_token_bearer_over_ssl_service_policy

图 14:OSB 代理服务策略
此策略要求 SAML 2.0 作为持有者并使用 SSL。
在 Security 选项卡中,用 OSTS 颁发方覆盖 saml.trusted.issuers 属性:
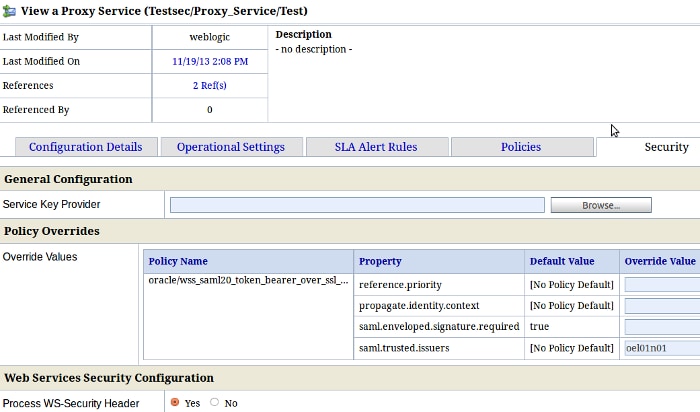
图 15:OSB 代理服务安全
OSB 收到的断言是用 OSTS 证书签名的。您必须从下面的 URL 获取此证书,并将其导入 Oracle Web Services Manager (OWSM) 密钥库:
http://<osts_host>:<osts_port>/sts/servlet/samlcert?id=osts_encryption&encoding=der
WebLogic Server
在本例中,客户端将使用策略 wss11user 从 OSTS 请求令牌,这要求按用户名进行身份验证,并使用 OSTS 证书对密码加密:
<?xml version="1.0"?>
<wsp:Policy xmlns:wsp="http://schemas.xmlsoap.org/ws/2004/09/policy"
xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd"
wsu:Id="wss11_username_token_with_message_protection_service_policy">
<sp:SymmetricBinding
xmlns:sp="http://schemas.xmlsoap.org/ws/2005/07/securitypolicy">
<wsp:Policy>
<sp:ProtectionToken>
<wsp:Policy>
<sp:X509Token
sp:IncludeToken="http://schemas.xmlsoap.org/ws/2005/07/securitypolicy/IncludeToken/Never">
<wsp:Policy>
<sp:RequireThumbprintReference />
<sp:WssX509V3Token11 />
</wsp:Policy>
</sp:X509Token>
</wsp:Policy>
</sp:ProtectionToken>
<sp:AlgorithmSuite>
<wsp:Policy>
<sp:Basic128 />
</wsp:Policy>
</sp:AlgorithmSuite>
<sp:Layout>
<wsp:Policy>
<sp:Lax />
</wsp:Policy>
</sp:Layout>
<sp:IncludeTimestamp />
<sp:OnlySignEntireHeadersAndBody />
</wsp:Policy>
</sp:SymmetricBinding>
<sp:SignedSupportingTokens
xmlns:sp="http://schemas.xmlsoap.org/ws/2005/07/securitypolicy">
<wsp:Policy>
<sp:UsernameToken
sp:IncludeToken=
"http://schemas.xmlsoap.org/ws/2005/07/securitypolicy/IncludeToken/AlwaysToRecipient">
<wsp:Policy>
<sp:WssUsernameToken10 />
</wsp:Policy>
</sp:UsernameToken>
</wsp:Policy>
</sp:SignedSupportingTokens>
<sp:Wss11 xmlns:sp="http://schemas.xmlsoap.org/ws/2005/07/securitypolicy">
<wsp:Policy>
<sp:RequireSignatureConfirmation />
<sp:MustSupportRefEncryptedKey />
</wsp:Policy>
</sp:Wss11>
<sp:SignedParts xmlns:sp="http://schemas.xmlsoap.org/ws/2005/07/securitypolicy">
<sp:Body />
<sp:Header Namespace="http://www.w3.org/2005/08/addressing" />
<sp:Header Namespace="http://schemas.xmlsoap.org/ws/2004/08/addressing" />
<sp:Header Name=
"fmw-context" Namespace="http://xmlns.oracle.com/fmw/context/1.0" />
</sp:SignedParts>
<sp:EncryptedParts
xmlns:sp="http://schemas.xmlsoap.org/ws/2005/07/securitypolicy">
<sp:Body />
<sp:Header Name=
"fmw-context" Namespace="http://xmlns.oracle.com/fmw/context/1.0" />
</sp:EncryptedParts>
</wsp:Policy>
</pre>
</div>
使用根据 OSB 代理服务 WSDL 文件和 OSTS 信息生成的存根类,我们可以创建 Web 服务客户端:
package test;
import java.io.File;
import java.net.URL;
import java.security.cert.X509Certificate;
import java.util.ArrayList;
import java.util.List;
import java.util.Map;
import javax.annotation.Resource;
import javax.jws.WebMethod;
import javax.jws.WebService;
import javax.xml.namespace.QName;
import javax.xml.soap.SOAPConstants;
import javax.xml.ws.BindingProvider;
import javax.xml.ws.WebServiceContext;
import org.example.test.Test;
import org.example.test.Test_Service;
import weblogic.jws.WLHttpTransport;
import weblogic.wsee.jaxrpc.WLStub;
import weblogic.wsee.message.WlMessageContext;
import weblogic.wsee.security.WSEESecurityConstants;
import weblogic.wsee.security.unt.ClientUNTCredentialProvider;
import weblogic.wsee.security.util.CertUtils;
import weblogic.xml.crypto.wss.WSSecurityContext;
import weblogic.xml.crypto.wss.provider.CredentialProvider;
@WebService
@WLHttpTransport(contextPath="TrustOSTSTest",
serviceUri="TrustOSTSTestService",
portName="TrustOSTSTestServicePort")
public class TrustOSTSTest {
private static final String TRUST_VERSION =
"http://docs.oasis-open.org/ws-sx/ws-trust/200512";
private static final String STS_URL =
"https://idm.oracleads.com:14101/sts/wss11user";
private static final String STS_POLICY =
"StsWss11Unt_OSTS_Policy.xml";
@Resource
private WebServiceContext context;
@WebMethod
public String hello(String text) throws Exception {
System.setProperty("javax.net.ssl.trustStore",
"/opt/oracle/workspace/wls/11g/domains/testsec/config/fmwconfig/soa-keystore.jks");
System.setProperty("javax.net.ssl.trustStorePassword", "weblogic");
File wsdlPath = new File("/opt/oracle/workspace/wls/projects/saml/
SamlClient/src/test/Test.wsdl");
URL wsdlURL = new URL("file:" + wsdlPath.getCanonicalPath());
QName serviceQName = new QName("http://www.example.org/Test/",
"Test");
Test_Service service = new Test_Service(wsdlURL, serviceQName);
Test test = service.getTestSOAP();
// Add the credential providers to the request context
Map<String, Object> requestContext =
((BindingProvider)test).getRequestContext();
// Oracle STS endpoint URL
requestContext.put(WLStub.WST_STS_ENDPOINT_ON_SAML, STS_URL);
// Oracle STS encrypt cert
requestContext.put(WLStub.STS_ENCRYPT_CERT, getServerCert());
// WS-Policy to talk to Oracle STS
requestContext.put(WlMessageContext.WST_BOOT_STRAP_POLICY,
this.getClass().getResourceAsStream(STS_POLICY));
// WS-Trust version
requestContext.put(WSEESecurityConstants.TRUST_VERSION, TRUST_VERSION);
// SOAP version
requestContext.put(WSEESecurityConstants.TRUST_SOAP_VERSION,
SOAPConstants.URI_NS_SOAP_1_2_ENVELOPE);
// username for whom a token will be requested
requestContext.put(WSEESecurityConstants.ON_BEHALF_OF_USER,
context.getUserPrincipal().getName());
List credProviders = buildCredentialProviderList();
requestContext.put(WSSecurityContext.CREDENTIAL_PROVIDER_LIST, credProviders);
return ("response: " + test.hello(text));
}
private static List buildCredentialProviderList() throws Exception {
List credProviders = new ArrayList();
credProviders.add(getClientUNTCredentialProvider());
return credProviders;
}
private static CredentialProvider getClientUNTCredentialProvider() throws Exception {
String username = System.getProperty("target.username", "weblogic");
String password = System.getProperty("target.password", "welcome1");
return new ClientUNTCredentialProvider(username.getBytes(), password.getBytes());
}
private static X509Certificate getServerCert() throws Exception {
String defaultServerCert = "/opt/oracle/workspace/wls/11g/domains/
testsec/osts_idm.der";
final X509Certificate cert =
(X509Certificate)CertUtils.getCertificate(defaultServerCert);
cert.checkValidity();
return cert;
}
}
以下几行代码定义了通过 WS-Trust 访问 OSTS:
requestContext.put(WLStub.WST_STS_ENDPOINT_ON_SAML, STS_URL);
requestContext.put(WLStub.STS_ENCRYPT_CERT, getServerCert());
requestContext.put(WlMessageContext.WST_BOOT_STRAP_POLICY, this.getClass() .getResourceAsStream(STS_POLICY));
requestContext.put(WSEESecurityConstants.TRUST_VERSION, TRUST_VERSION);
requestContext.put(WSEESecurityConstants.TRUST_SOAP_VERSION, SOAPConstants.URI_NS_SOAP_1_2_ENVELOPE);
此操作告诉 RST 在 WLS 中验证过的用户名,因此 OSTS 可以根据它创建 SAML 断言:
requestContext.put(WSEESecurityConstants.ON_BEHALF_OF_USER, context.getUserPrincipal().getName());
证书 osts_idm.der 用于构建发送给 OSTS 的 RST 时加密 usernametoken。
代码使用 soa-keystore.jks 作为受信任的密钥库。必须从该密钥库中的 OSTS 和 OSB 导入 SSL 证书。
Web 服务客户端必须要求身份验证,例如,这可以通过要求 BASIC 身份验证来实现,只需对 Web 描述文件略加修改。例如:
web.xml
<security-constraint>
<display-name>SecurityConstraint</display-name>
<web-resource-collection>
<web-resource-name>TrustOSTSTestService</web-resource-name>
<url-pattern>/TrustOSTSTestService</url-pattern>
</web-resource-collection>
<auth-constraint>
<role-name>everyone</role-name>
</auth-constraint>
<user-data-constraint>
<transport-guarantee>NONE</transport-guarantee>
</user-data-constraint>
</security-constraint>
<security-role>
<role-name>everyone</role-name>
</security-role>
<login-config>
<auth-method>BASIC</auth-method>
<realm-name>default</realm-name>
</login-config>
weblogic.xml
<wls:security-role-assignment>
<wls:role-name>everyone</wls:role-name>
<wls:principal-name>everyone</wls:principal-name>
</wls:security-role-assignment>
测试
将 Web 服务部署到 WebLogic 实例后,可以使用 pocsamlclient 用户对其进行测试。
测试时,WebLogic 会调用 OSTS,成功应答之后,调用 OSB:
return ("response: " + test.hello(text));
WebLogic 向 OSTS 发送一个 RST,类似下面所示(WLS 将在发送到 OSTS 之前对其进行加密):
<env:Body xmlns:env="http://www.w3.org/2003/05/soap-envelope"
xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd"
wsu:Id="Body_y3YwSoICSy12S1vl">
<wst:RequestSecurityToken
xmlns:wst="http://docs.oasis-open.org/ws-sx/ws-trust/200512">
<wst:TokenType>
http://docs.oasis-open.org/wss/oasis-wss-saml-token-profile-1.1#SAMLV2.0
</wst:TokenType>
<wsp:AppliesTo xmlns:wsp="http://schemas.xmlsoap.org/ws/2004/09/policy">
<wsa:EndpointReference xmlns:wsa="http://www.w3.org/2005/08/addressing">
<wsa:Address>
https://osb.oracleads.com:8012/Testsec/Proxy_Service/Test
</wsa:Address>
</wsa:EndpointReference>
</wsp:AppliesTo>
http://<osts_host>:<osts_port>/sts/servlet/samlcert?id=osts_encryption&encoding=der
<wst:Lifetime>
<wsu:Created>2013-11-21T13:33:45.243Z</wsu:Created>
<wsu:Expires>2013-11-21T13:34:45.243Z</wsu:Expires>
</wst:Lifetime>
<wst:KeyType>http://docs.oasis-open.org/ws-sx/ws-trust/200512/Bearer</wst:KeyType>
<wst:RequestType>http://docs.oasis-open.org/ws-sx/ws-trust/200512/Issue</wst:RequestType>
<wst:OnBehalfOf>
<wsse:UsernameToken
xmlns:wsse=
"http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd"
wsu:Id="unt_38uGcc6Uow5fCMIk">
<wsse:Username>pocsamlclient</wsse:Username>
</wsse:UsernameToken>
</wst:OnBehalfOf>
</wst:RequestSecurityToken>
</env:Body>
如果 OSTS 成功验证 RST,则使用 SAML Assertion 发送一个 RSTR。例如:
<env:Body xmlns:env="http://www.w3.org/2003/05/soap-envelope"
xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd"
wsu:Id="Body-27ud8azsQTUkMSMvp3x8TQ22">
<wst:RequestSecurityTokenResponseCollection
xmlns:wst="http://docs.oasis-open.org/ws-sx/ws-trust/200512">
<wst:RequestSecurityTokenResponse>
<wst:TokenType>http://docs.oasis-open.org/wss/oasis-wss-saml-token-profile-1.1#SAMLV2.0
</wst:TokenType>
<wst:RequestedSecurityToken>
<saml:Assertion xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion"
ID="id-1-HL01wfKQhzlwD-z-9IfJTO8d0-" IssueInstant="2013-11-21T13:33:45Z"
Version="2.0">
<saml:Issuer>oel01n01</saml:Issuer>
<dsig:Signature xmlns:dsig="http://www.w3.org/2000/09/xmldsig#">
<dsig:SignedInfo>
<dsig:CanonicalizationMethod
Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#">
</dsig:CanonicalizationMethod>
<dsig:SignatureMethod
Algorithm="http://www.w3.org/2000/09/xmldsig#rsa-sha1">
</dsig:SignatureMethod>
<dsig:Reference URI="#id-1-HL01wfKQhzlwD-z-9IfJTO8d0-">
<dsig:Transforms>
<dsig:Transform
Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature">
</dsig:Transform>
<dsig:Transform
Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#">
</dsig:Transform>
</dsig:Transforms>
<dsig:DigestMethod
Algorithm="http://www.w3.org/2000/09/xmldsig#sha1">
</dsig:DigestMethod>
<dsig:DigestValue>Bp00jLYXrUXzx6FAB6Jq6fq2+7Q=</dsig:DigestValue>
</dsig:Reference>
</dsig:SignedInfo>
<dsig:SignatureValue>glMt ... nI8M=</dsig:SignatureValue>
<dsig:KeyInfo>
<dsig:X509Data>
<dsig:X509Certificate>MIIB ... Z48V</dsig:X509Certificate>
</dsig:X509Data>
</dsig:KeyInfo>
</dsig:Signature>
<saml:Subject>
<saml:NameID
Format="urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified">
pocsamlclient
</saml:NameID>
<saml:SubjectConfirmation Method=
"urn:oasis:names:tc:SAML:2.0:cm:bearer">
</saml:SubjectConfirmation>
</saml:Subject>
<saml:Conditions NotBefore="2013-11-21T13:33:45Z"
NotOnOrAfter="2013-11-21T14:33:45Z"></saml:Conditions>
<saml:AttributeStatement>
<saml:Attribute Name="sn"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic">
<saml:AttributeValue xmlns:xsi=
"http://www.w3.org/2001/XMLSchema-instance"
xsi:type="xs:string">pocsamlclient
</saml:AttributeValue>
</saml:Attribute>
</saml:AttributeStatement>
</saml:Assertion>
</wst:RequestedSecurityToken>
<wsp:AppliesTo xmlns:wsp="http://schemas.xmlsoap.org/ws/2004/09/policy">
<ns2:EndpointReference
xmlns:ns2="http://www.w3.org/2005/08/addressing">
<ns2:Address>
https://osb.oracleads.com:8012/Testsec/Proxy_Service/Test
</ns2:Address>
</ns2:EndpointReference>
</wsp:AppliesTo>
<wst:RequestedAttachedReference>
<wsse:SecurityTokenReference
xmlns:wsse=
"http://docs.oasis-open.org/wss/2004/01/
oasis-200401-wss-wssecurity-secext-1.0.xsd">
<wsse:KeyIdentifier
ValueType="http://docs.oasis-open.org/wss/
oasis-wss-saml-token-profile-1.1#SAMLID">
id-1-HL01wfKQhzlwD-z-9IfJTO8d0-
</wsse:KeyIdentifier>
</wsse:SecurityTokenReference>
</wst:RequestedAttachedReference>
<wst:RequestedUnattachedReference>
<wsse:SecurityTokenReference
xmlns:wsse=
"http://docs.oasis-open.org/wss/2004/01/
oasis-200401-wss-wssecurity-secext-1.0.xsd">
<wsse:KeyIdentifier
ValueType="http://docs.oasis-open.org/wss/
oasis-wss-saml-token-profile-1.1#SAMLID">
id-1-HL01wfKQhzlwD-z-9IfJTO8d0-
</wsse:KeyIdentifier>
</wsse:SecurityTokenReference>
</wst:RequestedUnattachedReference>
<wst:Lifetime>
<wsu:Created>2013-11-21T13:33:45Z</wsu:Created>
<wsu:Expires>2013-11-21T14:33:45Z</wsu:Expires>
</wst:Lifetime>
<wst:KeyType>
http://docs.oasis-open.org/ws-sx/ws-trust/200512/Bearer
</wst:KeyType>
</wst:RequestSecurityTokenResponse>
</wst:RequestSecurityTokenResponseCollection>
</env:Body>
WebLogic 在 RSTR 中停用 SAML Assertion,并用它创建一条消息来调用 OSB:
<S:Envelope xmlns:S="http://schemas.xmlsoap.org/soap/envelope/">
<S:Header>
<work:WorkContext xmlns:work="http://oracle.com/weblogic/soap/workarea/">rO0A ... AAAA==
</work:WorkContext>
<wsse:Security
xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd"
S:mustUnderstand="1">
<saml:Assertion xmlns:dsig="http://www.w3.org/2000/09/xmldsig#"
xmlns:enc="http://www.w3.org/2001/04/xmlenc#"
xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion"
xmlns:x500="urn:oasis:names:tc:SAML:2.0:profiles:attribute:X500"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
ID="id-1-HL01wfKQhzlwD-z-9IfJTO8d0-"
IssueInstant="2013-11-21T13:33:45Z" Version="2.0">
<saml:Issuer>oel01n01</saml:Issuer>
<dsig:Signature>
<dsig:SignedInfo>
<dsig:CanonicalizationMethod
Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" />
<dsig:SignatureMethod Algorithm="http://www.w3.org/2000/09/xmldsig#rsa-sha1" />
<dsig:Reference URI="#id-1-HL01wfKQhzlwD-z-9IfJTO8d0-">
<dsig:Transforms>
<dsig:Transform
Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature" />
<dsig:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" />
</dsig:Transforms>
<dsig:DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha1" />
<dsig:DigestValue>Bp00jLYXrUXzx6FAB6Jq6fq2+7Q=</dsig:DigestValue>
</dsig:Reference>
</dsig:SignedInfo>
<dsig:SignatureValue>glMt ... nI8M=</dsig:SignatureValue>
<dsig:KeyInfo>
<dsig:X509Data>
<dsig:X509Certificate>MIIB ... Z48V</dsig:X509Certificate>
</dsig:X509Data>
</dsig:KeyInfo>
</dsig:Signature>
<saml:Subject>
<saml:NameID
Format="urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified">
pocsamlclient
</saml:NameID>
<saml:SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer" />
</saml:Subject>
<saml:Conditions NotBefore="2013-11-21T13:33:45Z"
NotOnOrAfter="2013-11-21T14:33:45Z" />
<saml:AttributeStatement>
<saml:Attribute Name="sn"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic">
<saml:AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema"
xsi:type="xs:string">pocsamlclient</saml:AttributeValue>
</saml:Attribute>
</saml:AttributeStatement>
</saml:Assertion>
<wsu:Timestamp
xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wsu:Created>2013-11-21T13:33:44Z</wsu:Created>
<wsu:Expires>2013-11-21T13:34:44Z</wsu:Expires>
</wsu:Timestamp>
</wsse:Security>
</S:Header>
<S:Body>
<ns2:hello xmlns:ns2="http://www.example.org/Test/">
<in>abc</in>
</ns2:hello>
</S:Body>
</S:Envelope>
OSB 根据 OSTS 证书验证签名,如果签名有效,则执行代理服务并向客户端返回响应:
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/">
<soapenv:Header>
<wsse:Security soapenv:mustUnderstand="1"
xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/
oasis-200401-wss-wssecurity-secext-1.0.xsd">
<wsu:Timestamp wsu:Id="Timestamp-Si0WdPuI4WlUbTbwbHAuhQ22"
xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/
oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wsu:Created>2013-11-21T13:33:47Z</wsu:Created>
<wsu:Expires>2013-11-21T13:38:47Z</wsu:Expires>
</wsu:Timestamp>
</wsse:Security>
</soapenv:Header>
<soapenv:Body>
<test:helloResponse xmlns:test="http://www.example.org/Test/">
<out>username = pocsamlclient, text = abc</out>
</test:helloResponse>
</soapenv:Body>
</soapenv:Envelope>
注:虽然 OSB 现在还不能使用 WS-Trust 策略,但除了 SSL 通信外,客户端 (WebLogic) 无需知道任何 OSB 特定的证书。要加密请求,客户端只需知道 OSTS 证书。因此,OSTS 仍是令牌管理的核心。
总结
本文介绍了如何配置和使用 OSTS 作为令牌生成器在 WLS 中的客户端以及 OSB 和 OWSM 提供的服务之间传播身份。
关于作者
Ronaldo Fernandes 是巴西 Oracle 顾问咨询部的首席顾问。他专门从事 Oracle 融合中间件、SOA 以及安全性工作,从 1996 年起就使用 Java 技术。他拥有超过 15 年的架构定义、问题解决以及技术领导和软件开发经验。![]()



