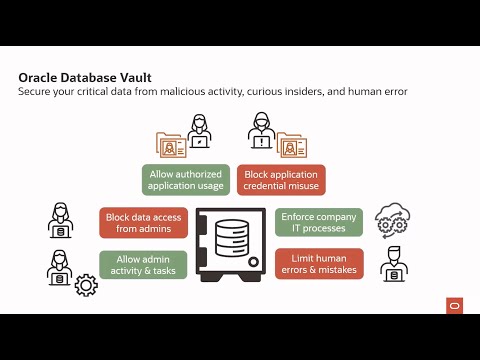
Database Vault
Oracle Database Vault enforces data security controls within Oracle Database to limit privileged user access to application data, reducing insider and external threats while meeting compliance requirements like separation of duties.
Explore KuppingerCole’s analysis of Oracle Database 23ai SQL Firewall, a new data-centric security solution
Why Oracle Database Vault
Protect sensitive data
Block unauthorized privileged access, including from scripts, tools, and AI agents, to sensitive data by enforcing restricted application realms in Oracle Database. Database Vault helps meet EU GDPR, PCI DSS, India DPDPA, and other mandates requiring strict internal controls over access, disclosure, and changes to sensitive information.
Prevent unauthorized database changes
Prevent malicious or accidental changes that disrupt operations by privileged user accounts. Command controls prevent unauthorized commands such as DROP TABLE or ALTER SYSTEM outside of specific maintenance windows.
Separation of duties
Enforce checks and balances on privileged users to prevent attackers from disabling security controls, creating rogue users, and accessing sensitive data by leveraging credentials from a single account.
Enforce trusted paths
Use factors like client IP, program, user, and time of day to enforce zero‑trust access to data and operations. Even with stolen credentials, attackers are blocked; Database Vault raises high‑value alerts on suspicious attempts to help stop data theft early.
Database Vault features
Database Vault can help you reduce the risk of insider and outside threats, address compliance requirements, including separation of duties, as well as minimize the potential of human error on application data and objects. Database Vault is built into the kernel of the Oracle database, thus ensuring you are implementing your security controls as close to the data as possible.
Realms
Realms serve as protection zones around sensitive database objects, ensuring that applications continue to function while preventing DBAs and other privileged users from viewing or altering data without explicit authorization.
Command Rules
Command rules let you control if, when, and how users can run nearly any SQL statement—SELECT, DDL, DML, ALTER SYSTEM, and more. Rule sets evaluate context to allow or block execution. In production, you can enforce stricter rules to prevent potentially disruptive commands (for example, ALTER SYSTEM or DROP/ALTER), reducing the risk of human error and unauthorized changes.
Simulation Mode
Validate Database Vault policies safely in Simulation Mode before deploying in production. Run in simulation mode to see exactly what would be denied by user, program, object, and time, so you uncover real dependencies and maintenance paths. Use the insights to tune realms, command rules, factors, and authorizations, and to build clean, auditable exception lists for owners, jobs, tools, and break‑glass procedures.
Operations Control
Oracle Database Vault operations control prevents common users from accessing application data in pluggable databases with one command.
Separation of Duties
Operations Control prevents common users from accessing application data in a pluggable database, so they can focus on safe fleet‑wide tasks like patching, backup, performance tuning, and configuration without viewing or changing sensitive records.
SQL Firewall
Mitigates risks from SQL injection attacks, anomalous access, and credential theft or abuse, preventing or detecting potential SQL injection attacks.
Resources
AskTOM Oracle Database Security Office Hours
AskTOM Office Hours offers free, open Q&A sessions with Oracle Database experts who are eager to help you fully leverage the multitude of enterprise-strength database security tools available to your organization.

LiveLabs Workshop: Oracle Database Vault
This workshop introduces Oracle Database Vault's features and functionality. Explore how to configure Database Vault to protect databases and the sensitive data contained therein with features like realms and trusted paths. Run this workshop on your own tenancy or reserve a time to run the workshop on LiveLabs, free of charge.

The Achilles Heel of Cybersecurity: Lessons from a Recent Data Breach
Vipin Samar, Senior Vice President, Database Security, Oracle and Russ Lowenthal, Vice President, Database Security, OracleUnlike providers that leave gaps and require you to piece together disparate security technologies, Oracle offers a defense-in-depth strategy with a suite of best-in-class, integrated security components that aims to support you in seamlessly protecting your data everywhere.
Featured database security blogs
- October 14, 2025Celebrating 5 Years of Innovation with Oracle Audit Vault and Database Firewall (AVDF)
- October 10, 2025Oracle Key Vault: Extending deeper into your environment
- October 9, 2025Simplifying Database Security Compliance at Scale with Oracle Data Safe
- October 8, 2025Securing Oracle AI Database 26ai for the Quantum Era
- Continue readingSee all
Get started with Oracle database security
Try Database Vault
Experience Database Vault by configuring your key use cases on LiveLabs. This lab focuses on limiting data access by DBA and privileged users, restricting database command execution, and preventing a multitenant common user from accessing objects in pluggable databases.
Try SQL Firewall
Experience Oracle Database 26ai SQL Firewall, a kernel-integrated defense that blocks SQL injection, credential misuse, and unauthorized access with no agents, bypasses, or dependencies. This workshop teaches how to manage SQL Firewall and monitor violations using real-world scenarios.
Try Database Vault on Autonomous Database
Experience Database Vault on Autonomous Database. This workshop focus on key areas including enforcing separation of duties, restricting privileged user operations, and applying contextual controls based on SYS_CONTEXT attributes such as IP address, hostname, and OS user.
Contact sales
Talk to a team member about Oracle Database security.