Label Security
Control what data users see based on data and session labels. Oracle Label Security records and enforces access permission for data based on project codes, regions, or data classifications. These controls reduce the risk of unauthorized access to sensitive data and help to demonstrate regulatory compliance.
2025 KuppingerCole Leadership Compass for Data Security Platforms
Discover why KuppingerCole recognized Oracle as a Leader in database security
Why Label Security
Enforce need-to-know access
Label Security implements multi-level access controls based on data classification and user access labels, applying mandatory, classification-based row access directly in Oracle AI Database
Simplify compliance
Policies help meet GDPR and industry mandates by controlling who can access and process data—isolating subject data, preventing unauthorized processing, and enabling deletion or anonymization workflows. Oracle Label Security, as part of Oracle AI Database, has been consistently evaluated under Common Criteria (ISO/IEC 15408).
Secure data segregation
Support multi-tenant and shared-schema use cases by isolating tenants, business units, or regions within the same tables.
Consistent security policies across applications
Reduce application development time by leveraging a centralized data security model enforced at the core data layer.
Label Security features
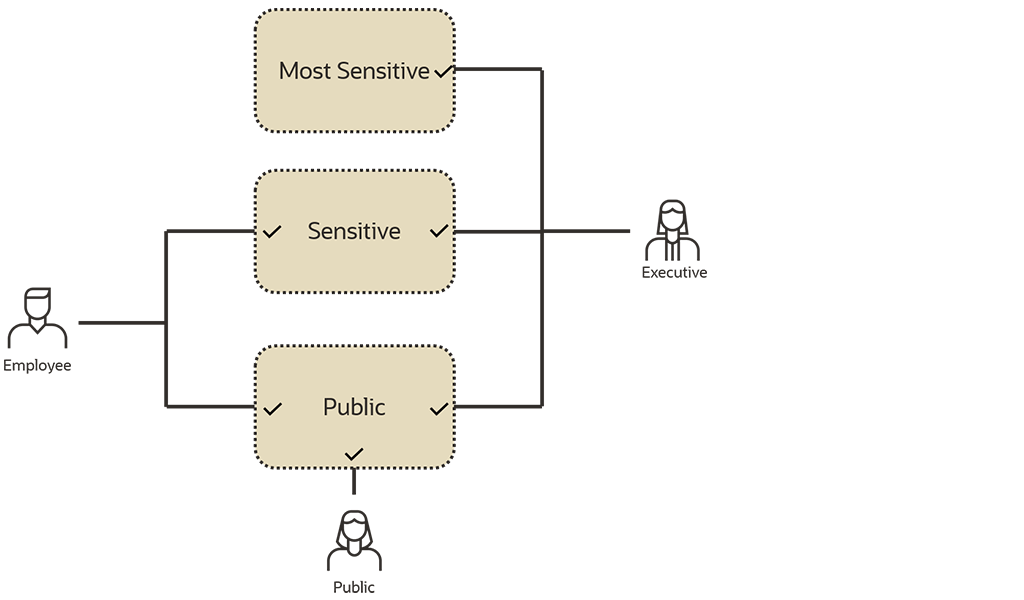
Label Security can help you enforce classification-based, row‑level access in Oracle AI Database to implement need‑to‑know access without changing applications, reduce insider risk, and meet privacy mandates like GDPR’s right to restriction of processing and track right to erasure. Oracle Label Security controls data access based on the identity and label of the user, and the sensitivity and label of the data. It supports tenant and data segregation in shared schemas allowing organizations to reduce operational and storage costs by securely storing data of varying sensitivity levels within a single database.
Classification-based row access
Attach a data label to each row using sensitivity levels plus compartments and groups for flexible policies that match your organization and data access needs.
User clearances and authorizations
Assign maximum, default, and read/write label authorizations so each user’s access aligns to their clearance.
Read and write enforcement
Enforce label checks on SELECT, INSERT, UPDATE, and DELETE; block cross-label writes and unauthorized changes to reduce insider risk and human error.
Session labels and context controls
Set a session label to constrain what a user can read/write at runtime; optionally combine with session context (e.g., program, IP, time) for stricter paths.
Automatic labeling and inheritance
Default or derive row labels during insert/update, inherit labels across related rows, and ensure data is correctly labeled
Central administration and auditing
Manage policies, labels, and clearances via admin APIs and Oracle Enterprise Manager; emit auditable events and integrate with Oracle auditing/AVDF.
Resources

AskTOM Oracle Database Security Office Hours
AskTOM Office Hours offers free, open Q&A sessions with Oracle Database experts who are eager to help you fully leverage the multitude of enterprise-strength database security tools available to your organization.
LiveLabs Workshop: Oracle Label Security
This workshop introduces Oracle Label Security features and functionality. Explore how to create a label policy that defines user clearances and data labels for a privacy mandate, apply the policy to a table, attach labels to existing records, and understand how levels, compartments, and groups combine to form labels that drive access decisions.

The Achilles Heel of Cybersecurity: Lessons from a Recent Data Breach
Vipin Samar, Senior Vice President, Database Security, Oracle and Russ Lowenthal, Vice President, Database Security, OracleUnlike providers that leave gaps and require you to piece together disparate security technologies, Oracle offers a defense-in-depth strategy with a suite of best-in-class, integrated security components that aims to support you in seamlessly protecting your data everywhere.
Featured database security blogs
- October 14, 2025Celebrating 5 Years of Innovation with Oracle Audit Vault and Database Firewall (AVDF)
- October 10, 2025Oracle Key Vault: Extending deeper into your environment
- October 9, 2025Simplifying Database Security Compliance at Scale with Oracle Data Safe
- October 8, 2025Securing Oracle AI Database 26ai for the Quantum Era
- Continue readingSee all
Get started with Oracle database security
Try Label Security
Experience Label Security by configuring your key use cases on LiveLabs. In this hands-on lab, you’ll create a label policy that defines user clearances and data labels for a privacy mandate, apply it to a table, attach labels to existing rows, and learn how levels, compartments, and groups combine to drive access decisions.
Try Database Vault
Experience Database Vault by configuring your key use cases on LiveLabs. This lab focuses on limiting data access by DBA and privileged users, restricting database command execution, and preventing a multitenant common user from accessing objects in pluggable databases.
Run Oracle Database Security Assessment Tool
Quickly assess database security posture and get recommendations to mitigate risks.
Contact sales
Talk to a team member about Oracle Label Security.
