Database Security Assessment Tool
Oracle Database Security Assessment Tool provides prioritized recommendations on how to mitigate identified security risks or gaps within Oracle Database. The tool profiles the security and compliance posture of databases by evaluating the current state, including configuration, discovering sensitive data, and more.
On-demand webinar: Leveraging DBSAT 4.0 to enhance your Oracle Database security
Why Oracle Database Security Assessment Tool
Identify database risks
Identify misconfigurations, excessive user privileges, and database security policies in place, and get recommendations to improve your overall database security posture.
Discover sensitive data
Get started with discovering and classifying regulated sensitive data across multilingual data dictionaries in English, Dutch, French, Greek, Italian, German, Portuguese, and Spanish.
Accelerate regulatory compliance
Streamline alignment with Oracle Database security best practices, Defense Information Systems Agency Security Technical Implementation Guides (STIGs), Center for Internet Security (CIS) Benchmarks, and data privacy regulations, such as the EU’s GDPR.
The perfect starting point
DBSAT is a great starting point for assessing Oracle Database security on a few databases. For broader, enterprise-ready needs, Audit Vault and Database Firewall and Data Safe offer fleet-wide assessments, baselines, drift reports, filtering, comparisons, and more.
DBSAT features
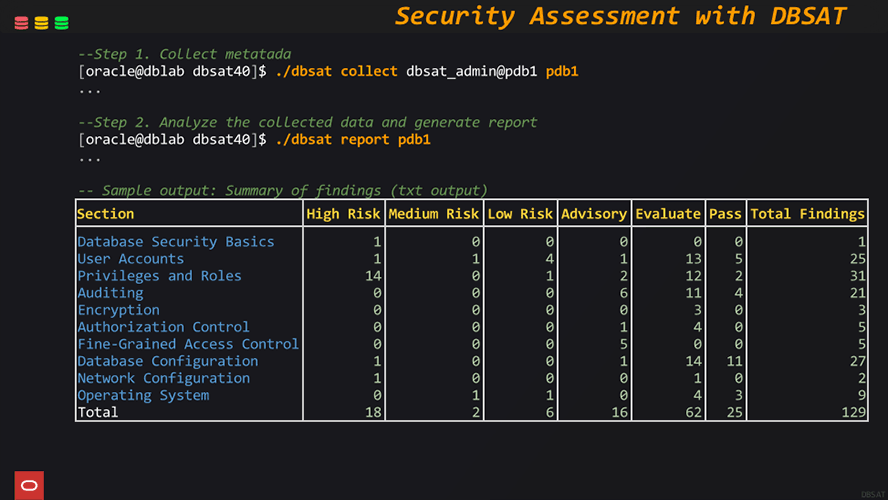
DBSAT can help you get started with understanding and assessing the security posture of your Oracle Databases. By performing on-demand reviews, DBSAT helps identify risks related to configurations, privileges, and data exposure. DBSAT’s detailed reports help organizations meet compliance standards and document their security practices for auditors and stakeholders.
Security Assessment
DBSAT evaluates key aspects of Oracle Database, including configurations, user access, roles, and data sensitivity, offering a comprehensive security risk overview.
Sensitive Data Assessment
Identifies and analyzes sensitive data within the database to help organizations understand and protect their data landscape.
Flexible, Readable Reports
DBSAT generates user-friendly reports in HTML, JSON, CSV, and TXT formats, facilitating easy sharing with security teams, DBAs, and auditors for continuous monitoring and compliance tracking.
Risk-Based Advice
Based on its findings, DBSAT provides clear, prioritized recommendations by risk level enabling organizations to effectively tackle critical security issues.
Best Practices and Security Frameworks
DBSAT helps organizations align Oracle Database security with industry standards like the CIS Benchmark, DISA STIG, and Oracle best practices by assessing configurations and user privileges, identifying gaps, supporting control implementation, and providing actionable guidance to enhance security and ensure compliance
Simple to Use
With a lightweight footprint and no need for extensive configuration, DBSAT can be quickly executed on databases, empowering teams to conduct rapid assessments with minimal disruption.
Resources
AskTOM Oracle Database Security Office Hours
AskTOM Office Hours offers free, open Q&A sessions with Oracle Database experts who are eager to help you fully leverage the multitude of enterprise-strength database security tools available to your organization.

LiveLabs Workshop: Oracle DBSAT
This workshop introduces Oracle Database Security Assessment features and functionality. Explore how to run DBSAT and learn how to assess the security posture of your Oracle Database and discover sensitive data. Run this workshop on your own tenancy or reserve a time to run the workshop on LiveLabs, free of charge.

Simplify STIG compliance checks with the new Database Security Assessment Tool (DBSAT) version 4.0
Pedro Lopes, Senior Principal Product Manager, Database Security, OracleSecuring your databases shouldn’t be a guessing game. For IT admins, DBAs, and security professionals, the pressure to prevent data breaches, pass audits, and keep up with evolving standards like DISA STIG is relentless. As threats and compliance requirements grow more complex, closing configuration gaps is more critical than ever. Since its debut in 2016, the Database Security Assessment Tool (DBSAT) has helped many organizations worldwide meet audit, compliance, and advanced security goals.
Featured database security blogs
- October 14, 2025Celebrating 5 Years of Innovation with Oracle Audit Vault and Database Firewall (AVDF)
- October 10, 2025Oracle Key Vault: Extending deeper into your environment
- October 9, 2025Simplifying Database Security Compliance at Scale with Oracle Data Safe
- October 8, 2025Securing Oracle AI Database 26ai for the Quantum Era
- Continue readingSee all
Get started with Oracle database security
Try DBSAT
Experience DBSAT by configuring your key use cases on LiveLabs. Explore how to run DBSAT and learn how to assess the security posture of your Oracle Database and discover sensitive data.
Try Data Safe
Experience Data Safe by configuring your key use cases on LiveLabs. This workshop guides you through the main features in Oracle Data Safe, including Security Assessment, User Assessment, Data Discovery, Data Masking, Activity Auditing, Alerts, and SQL Firewall.
Try Audit Vault and Database Firewall
Experience Audit Vault and Database Firewall by configuring your key use cases on LiveLabs, where you'll learn to assess, monitor, and protect enterprise databases while receiving notifications of unauthorized activities
Contact sales
Talk to a team member about Oracle Database security.
